Firewalls have been used for decades as protection from attacks. Their applications range from home usage protecting users from outside attacks to big corporations and servers acting in the same manner. While the firewall is designed to keep certain things locked outside, it can do the same in reverse.

There are firewalls set to block user access to specific websites and servers. It does that by locking the port or destination IP address disabling the access. These kinds of limitations can be found in libraries, work offices, or sometimes in a home network. The good news is that there are ways to remove them.
In today’s article, we are going to discuss several approaches to bypassing a firewall restriction. Some are easier to set, while others may require you to download additional software and may pay for it.
Since firewalls act as a two-way filter, what we will do today will affect the filter blocking outgoing packets.
VPN
A VPN is often the most common and easiest way of bypassing a firewall restriction.
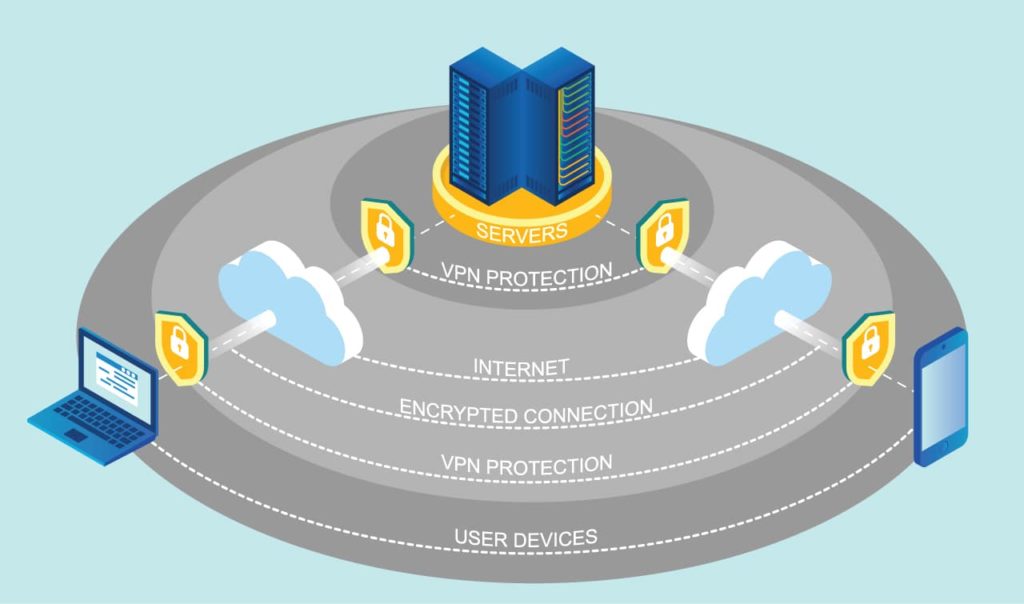
A VPN is a Virtual Private network that the service creates for your connection. It works as a tunnel where all the data you send gets encrypted before “exiting” your device. The tunnel works as a two-way street encrypting the data from and to your device.
When you access a website, the request packages are front from your device to the destination server. In the VPN case, they go to the VPN server, which reroutes them to the site you want to access. By doing this, the firewall sees that you are trying to access something else. For example, if the firewall filters Facebook, every time you type in the URL, the firewall will block it. If you have a VPN active, the firewall will see a request to go to a non-Facebook IP address, and you will have no problem with it.
The advantage of using a VPN is that despite the firewall bypass, you also get additional security. The use of the tunnel means that the data remains encrypted until it reaches the destination. Even if someone manages to intercept the packages, they won’t be able to decrypt them.
When it comes to choosing a VPN for bypassing a firewall, the choice is vast. There are some free options, but the free options are not always the best, as we often advise our readers. Getting something for free doesn’t mean that the company is generous. It means that it will not make a profit from selling the product to you. Instead, it will resort to other ways of making money. Another distrust we have is that the data may be used for different kinds of activities. Both of these can be avoided by purchasing a VPN.
You have providers like ExpressVPN, NordVPN, Surf Shark, and tons more that will provide you with excellent service for a relatively low price. Some may offer a free trial or a free account with a limited amount of bandwidth included.
Another thing to consider is how you plan to use it. If you need a VPN for firewall bypassing on a system-wide level on your device, then you need the dedicated app. On the other hand, you can also use a browser extension.
Proxy
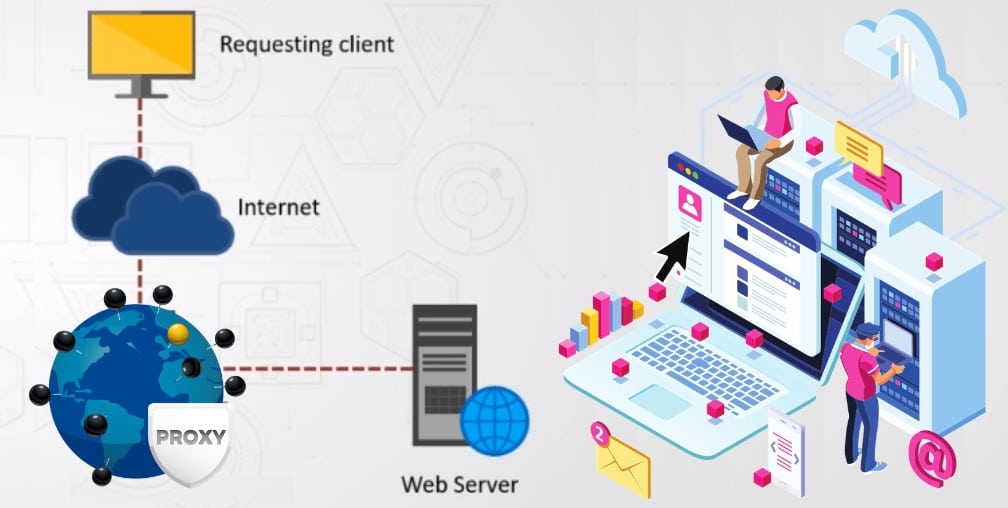
Proxy is another effective way of bypassing firewall restrictions. A proxy server is like a gateway between your device and the internet. When you send out a package request for a website, they go to the proxy server that redirects them through the actual proxy address and then goes to the destination. The longer route the packets go through means that you may end up with slightly higher latency.
Also, since they are just the gateway, there is no encrypted tunnel that carries the data packages.
The proxy address that you get can either be a data center, residential or mobile. The datacenter is the fastest as they are on the server itself. Residential and mobile proxies are IP addresses from people that got them from the ISP. These are the slower ones but are less likely to get detected.
Read more, Different between Datacenter Proxies and Residential Proxies.
When it comes to choosing proxies, you get a lot of flexibility. On the datacenter side of things, you have MyPrivateProxy, HighProxies, BuyProxies, InstantProxies, and many more. If you want a residential or mobile, you should go to Luminati, Soax, Smartproxy, Stormproxies, etc.
Related,
Setting up the proxy to bypass a firewall can be slightly problematic. Some providers may have a browser extension, but if you need a system-wide proxy, you’ll have to get your hand dirties a bit.
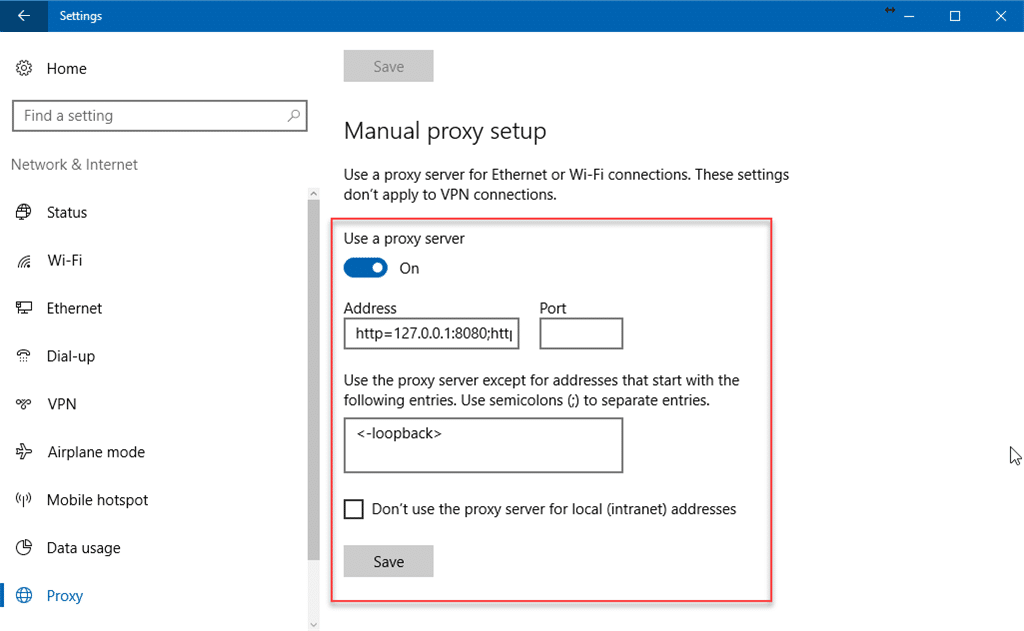
On Windows, head over to “Settings” and then “Network & Internet.” From the left navigation panel, go to “Proxy” and locate “Manual proxy setup.” Enable the toggle that says “Use a proxy server” and enter the proxy address and port. You can exclude some addresses and enable them not to be used for local addresses. Once everything is set up, click save, and you’re good to go.
On Mac, open up the “System Preferences” and navigate to “Network.” In the new window from the left side, you will need to choose the network connection that you want to apply the proxy. Once selected, click on “Advanced” and click on the tab named “Proxies.” On the left side, choose which protocol you want the proxy to apply and enter the required information on the right. To save the settings, click “OK.”
If you are a Linux user, the process will depend on the distribution you are using.
TOR

The Onion Router is a network that enables you to browse the internet anonymously. To utilize the network, you will need to download and install the browser, and you’ll be good to go.
TOR works similarly to a proxy network, but you are getting them for free instead of paying for them. The network consists of volunteers that “share” their IP addresses that act as proxy addresses. Unlike a regular proxy, where the data is routed through one IP address, with TOR, it gets bounced around. The data gets passed around through several proxy addresses before it reaches its destination.
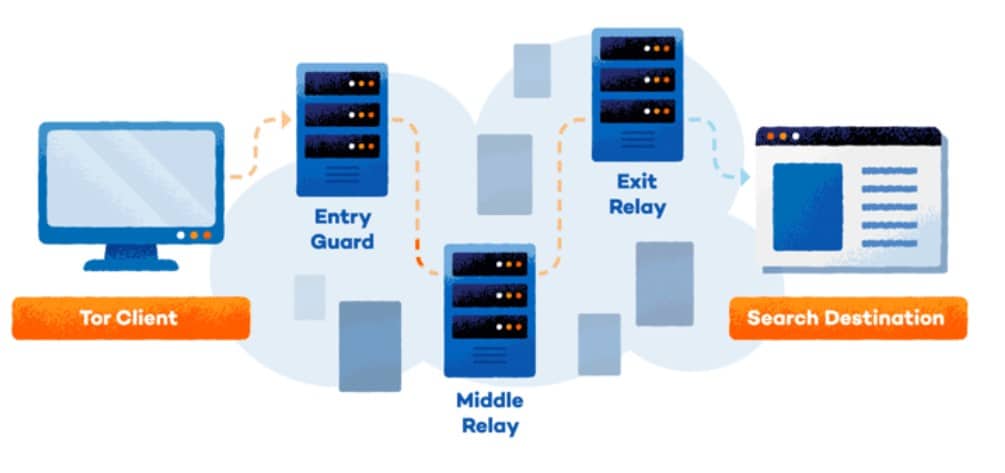
The feature increases anonymity and will certainly bypass any firewall restriction, but there is a price to pay. We mentioned that going through one proxy will have an impact on speed and latency. Going through several will make things worse, meaning that you may not have the best browsing experience.
Use a Different Connection
Changing the connection may have some results when it comes to bypassing a firewall. The easiest and most straightforward way to do so is to use your phone’s connection. You can set up your phone as a tethering device via a cable, or you can create a WiFi hotspot.
Both ways work just fine; the difference is how you want to have things connected. Keep in mind that some plans come with a limited amount of bandwidth. It would be best if you kept an eye on the limit to avoid additional expenses.
Depending on your location and the device you are using, you may have some luck with a neighboring WiFi. Try to be careful with open networks, as the data sent through that can be intercepted.
Change the Settings
In almost all cases, the firewall settings are part of the router that you are connected to. If you happen to have access to the router, you can easily change them and remove the limitations. There are a few things you’ll need before you start making changes.
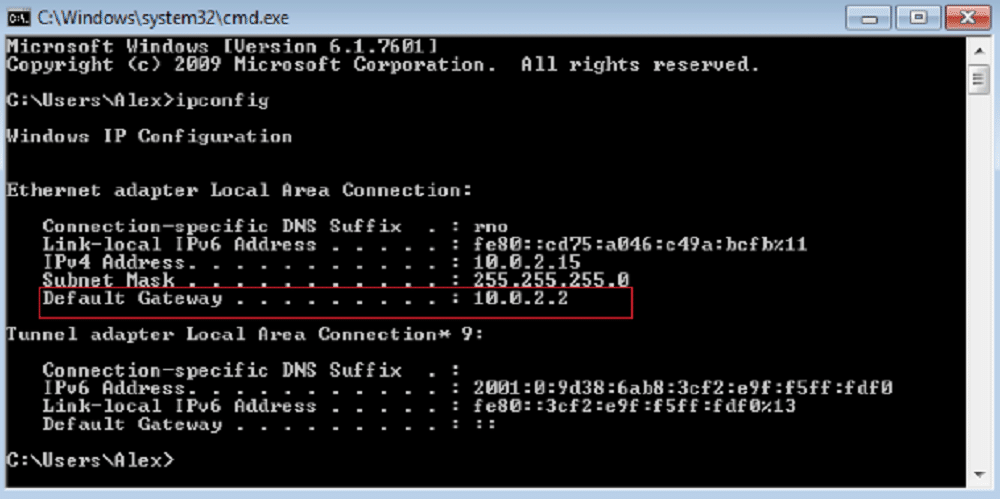
If you have the router’s login credentials, things are easy; otherwise, you may need to get creative. Before that, you’ll need the router’s IP address. To find it, you’ll need to open the command prompt on Windows or Terminal on Mac and Linux. The Windows command is “ipconfig,” for Mac it’s “netstat -r,” and on Linux, it’s “IP r.” When you get the information, you should be looking for the IP address associated with the “Default Gateway.”
The following information you need to find is the make and model of the router. Unfortunately, you cannot get this info with a few lines of code. If you have physical access to the router, check the sticker on the bottom, which will contain the make model and some additional info. Alternatively, you can enter the IP address you found as the default gateway, and you may find the information you need. Worst case scenario, you’ll have the make.
The login credentials can be problematic. Some people don’t change the factory username and password, meaning that you can find them with a quick Google search. If they are changed, then this will not work.
Let’s say you managed to find all the necessary info, and you successfully logged in to the router’s dashboard. There are tons of router manufacturers, meaning there are multiple ways of making these changes. In most cases, the settings should be under security or firewall, where you will have an option for website block.
It takes some work and research, and the user manual of the router can be your best friend.
Should you Bypass Firewall?
That is the million-dollar question. In certain situations, websites and services are restricted to prevent wasting time being unproductive. A library or office may block websites to ensure that you study or be productive, not spend time browsing social media. You risk getting some kind of disciplinary action taken against you.
There are some other risks involved. Depending on the type of firewall bypass you use, you can open yourself to getting your data stolen, getting spied on, and so on.
Overall, the firewall’s goal is to keep you protected, and when you bypass it, you open yourself up to threats.
Frequently Asked Questions About Firewall Bypassing
Is firewall bypassing legal?
Yes. There are no laws that prohibit you from bypassing the restrictions set by the firewall. With that said, it is something that could go against your company or school’s policy. It means that if you get caught, you can get in trouble.
Can I use free proxies?
We often recommend against using free proxies. It usually means that you’ll be getting IP addresses where you have no idea who will be managing them. Free proxies are the least safe way of bypassing firewall restrictions.
Any specific requirements for VPNs or proxies?
It depends on what you want to access. Most VPN and proxy providers will have IP addresses in multiple locations around the world. If you need to access a website or service which is limited to a specific country, make sure to go for a service with IPs in that country.
Apart from that, you should also keep in mind the speed. If you want to stream from a service, you’ll need a proxy or VPN that will work with the service in question. On top of that, you should check the speeds that the services offer. Lower speeds and higher latency will have a terrible impact on your streaming experience.
How safe is it to bypass a firewall?
It mostly depends on the site you want to reach. If you are trying to bypass a firewall restriction to access social media or video streaming sites, then you are safe. On the other hand, administrators tend to limit access to illicit sites where you can get scammed or get your PC infected. In that case, you will be open to risks.
What will happen if a completely disable the firewall?
The firewall software on your computer is intended to keep you protected. Completely disabling it means that your connection will be open to attacks.
Will disabling a firewall open all ports?
Yes. Disabling the firewall will entirely open all ports. It means that all traffic going through them will remain unmonitored, and there will be nothing protecting you from attacks.
Is it better to have two firewalls?
It depends. Two software firewalls on your computer are not recommended because they can often work against each other. On the other hand, having a firewall on your WiFi router and your computer is the double layer of security that you’d want to have.
Conclusion
Firewalls can be your greatest ally or your worst enemy. On the one hand, they protect you from outside attackers, and on the other hand, they can block your access to some sites.
The first reason is not good enough for you to try and go around it, but the second one is. Lucky for you, we compiled a bigger list of ways to bypass a firewall and get access to your favorite websites or services.
