LimeProxies Review
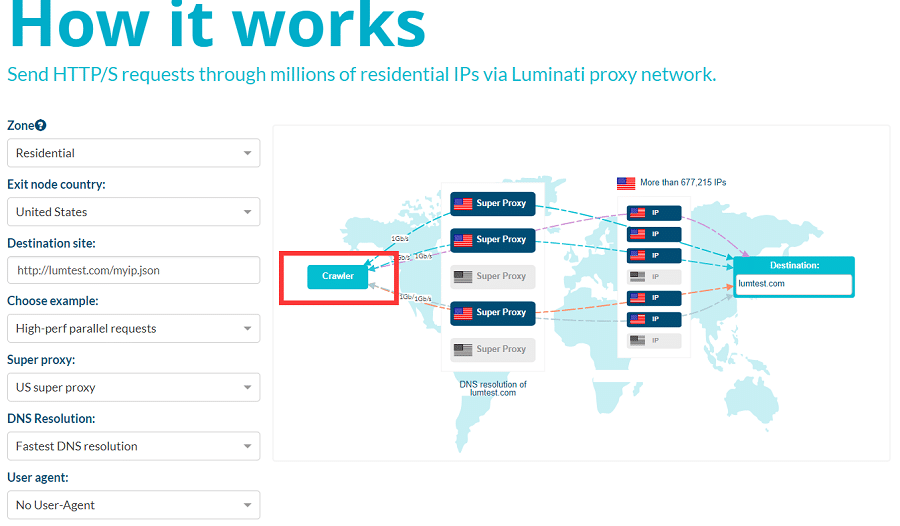
We DO not recommend you use limeproxies! Our project was destroyed by their Bad Proxies! 100% stay away! [Updated Dec 11, 2019] Out of many proxy services currently operating worldwide, it’s often very hard to choose the right proxy service that is suitable for one’s needs. While some proxies are suitable for specific tasks, sometimes …