We know that VPN ensures the security of users on public connections such as the internet, but how exactly do they do it? A VPN creates a secure path “tunnel” that encrypts the private data, separating it from other internet traffic. It is not a physical path but a logical construct that uses protocols, security standards, and encryption.
The best way to protect your information is never to share it over a public network, but we all know it is nearly impossible. That’s why we take the aid of VPNs to secure our online journey. This deters threat actors and allows the IT teams to troubleshoot any threats that have already entered the system. This guide will discuss VPN tunneling, its protocols, and whether it really keeps your online information confidential.
What is VPN Tunneling?

It is a process that enables secure data transmission through an insecure environment (internet) without compromising its privacy. These protocols are a set of standardized rules and policies employed on transmitted data. VPN tunneling encrypts data, making it difficult for any unauthorized person to comprehend and use it.
However, this doesn’t mean any physically wired infrastructure is there to pass data through the insecure environment. Rather, it follows data encryption and data encapsulation principles to carry data within a public network safely.
Data encapsulation protects your data from other data packets on the internet, while encryption makes it unreadable, even for criminals and surveillance agents.
Different VPN Tunneling Protocols
Compare table for the VPN tunneling protocols
| Protocol | Speed | Security | Ease of Use | Blockage |
|---|---|---|---|---|
| PPTP | Fast | Low | Easy | Prone to blocking |
| L2TP/IPSec | Slower than PPTP | High | Moderate | Fixed ports prone to blocking |
| SSTP | Moderate | High | Easy | Difficult to block |
| IKEv2/IPSec | Fast | High | Easy | Prone to blocking |
| OpenVPN | Moderate to Fast | High | Moderate | Can traverse VPN-blocking software |

A tunneling protocol is a software that sends or receives data among different networks. Some protocols excel in speed but are not much secure, and vice versa.
Some of the most popularly used VPN tunneling protocols are;
Point-to-Point Tunneling Protocol (PPTP)
PPTP is one of the fastest, oldest, and most popular VPN tunneling protocols. Moreover, the configuration is easy as it only requires a username, password, and server address to build a secure tunnel for the remote server.
Its low encryption facilitates huge speed but a compromised level of security. Therefore, it should be utilized in networks where speed is more important than security. Most companies integrate additional security while using PPTP due to its low level of security.
Layer 2 Tunneling Protocol (L2TP)/Internet Protocol Security (IPSec)
Layer 2 Tunneling protocol does not provide data confidentiality by itself, but it combines with another protocol to create two layers of encryption. The other tunneling protocol involved is Internet Protocol Security, which is collectively called L2TP/IPsec.
Though it offers ultimate security, double encryption makes data transmission slower than PPTP. Moreover, it can face bypassing restrictions as it uses fixed ports prone to becoming identified by VPN-blocking software.
Secure Socket Tunneling Protocol (SSTP)
SSTP embraces a strong encryption procedure, making it one of the safest VPN tunneling protocols available on the Windows operating system by default. Another advantage of SSTP is that it is difficult to block it, as the traffic is transmitted via a popular web connection, that is HTTP.
Internet Key Exchange (IKEv2)/Internet Protocol Security (IPSec)
Though seem to be an enhancement of the LT2P protocol, IKEv2 incorporates some of the strongest encryption methods available, moreover, it is faster than LT2P and offers a smooth and easier reconnection of the system that has been interrupted.
Moreover, it works in combination with IPSec to ensure ease, stability, and speed. However, it is also prone to blockage.
OpenVPN
It is also a popular protocol developed using open-source software. It utilizes Secure Socket Layer (SSL) encryption protocol to guarantee that data traffic between two devices is private. The best property of OpenVPN is that it can traverse VPN-blocking software. As it is an open-source protocol, experts keep upgrading it with the latest security features to boost user confidence in the protocol.
OpenVPN requires third-party software to configure it. However, if you seek the services of a reliable VPN service provider, such as Nordlayer, you won’t need to bear these hassles. Just install the app, and the protocol is readily available to you.
Which tunneling protocol is the Best?
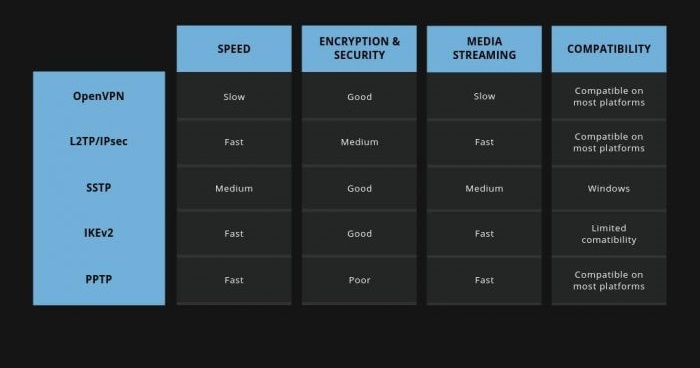
Every tunneling protocol has its own benefits and drawbacks. PPTP has high speed but compromised security. L2TP/IPSec has secure encryption but finds some difficulty in dealing with firewalls due to its fixed ports.
SSTP is only available to Windows users, while OpenVPN needs a third-party client app that is not supported by all operating systems. Therefore, you should gauge your security and data transmission requirements to ensure which tunneling protocol can serve you the best
A good VPN offers three to four choices of tunneling protocols for your online activity. Moreover, you should look for an affordable option that provides you with the requisite privacy and security.
Final Words
VPN tunneling allows users to share data on insecure networks like the internet safely. It encrypts and encapsulates your data and helps you browse the internet, share data, and access blocked websites.
The degree of speed, security, and bypassing ability depends on your choice of tunneling protocols. PPTP, L2TP/IPSec, SSTP, and OpenVPN are some of the widely used tunneling protocols, their specific use cases, and side hassles, such as installing third-party apps or slower speeds.
When you opt for a reliable VPN provider, you are provided several VPN tunneling protocol options. The VPN you choose should offer some of all the above-mentioned tunneling protocols to get an enhanced level of security and privacy.